Cyber Ranges
Emulating your production environment provides security teams with a safe area to test tools, develop, and learn, yet, facilitating these types of environments in-house can be a drain on resources.
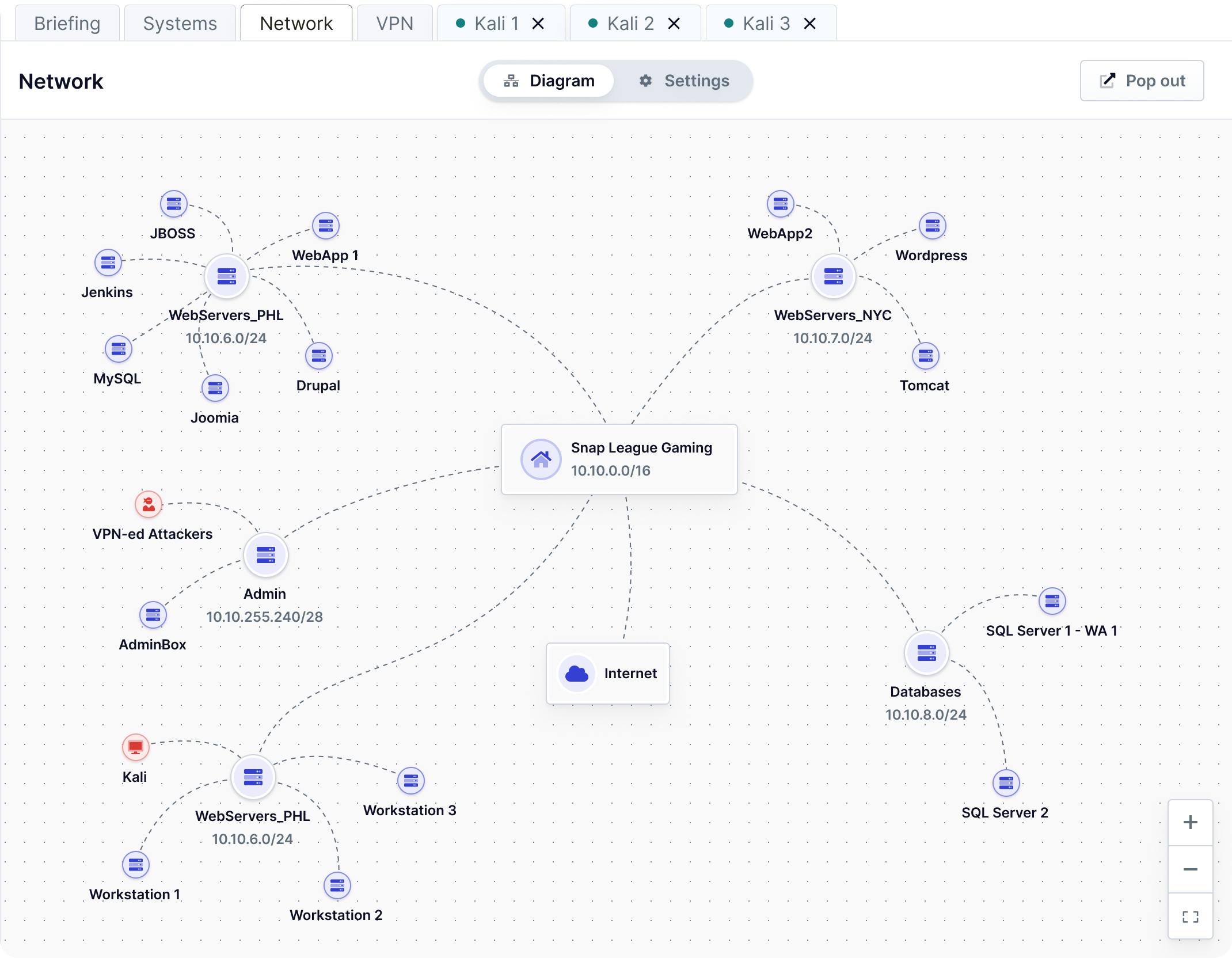
Immersive Labs Cyber Ranges enables you to build customizable environments, available on demand when you need them. Create complex ranges in hours, not weeks, with minimal maintenance.
Build in hours, launch in minutes
Immersive Labs Cyber Ranges provides you with on-demand access to your custom ranges in minutes: your environments are available when you need them and automatically
power down when you don’t.
Bring in your own tools and vendors
Cloud-based networks can be customized to meet your team’s needs and emulate virtually any target environment. Whatever your use case, ensure the highest relevance by bringing existing tools and vendors into a range.

Emulating your production environment provides security teams with a safe area to test tools, develop, and learn, yet, facilitating these types of environments in-house can be a drain on resources.
Immersive Labs Cyber Ranges enables you to build customizable environments, available on demand when you need them. Create complex ranges in hours, not weeks, with minimal maintenance.
We no longer worry about managing infrastructure, leaving us free to build great courses.
– Daniel Duggan, Director, Zero-Point Security
Research and development
Immersive Labs’ Cyber Ranges are customized for your team’s needs, remove roadblocks and time-consuming network setup activities that prevent teams from executing on your organization’s vision.
These realistic and customizable environments mean you can easily conduct high- fidelity basic or applied research.
Build exercises for teams
Give your teams access to powerful testing environments without requiring on-premise networks. Cloud-based cyber ranges is easily accessible from anywhere via the browser or a VPN connection, making them an ideal solution for remote or distributed teams.
Onboarding
Immersive Labs Cyber Ranges lets you build assessment environments to accurately measure candidate aptitude, or onboard new hires, in the specific areas you care about most. Provide intuitive and easy-to-access environments without the need for on-site visits or special hardware requirements. Perfect for a growing remote workforce.
Defensive security workforce resilience
Immersive Labs is a cyber workforce resilience platform enabling a cycle of exercising, evidencing, and equipping across your organization, including blue teams. They need to be informed about the latest risks to your organization and be confident in tackling them whenever they strike.
Immersive Labs Cyber Workforce Resilience Platform